Add to Favorites Portecle is a user friendly GUI application for creating, managing and examining keystores, keys, certificates, certificate requests, certificate revocation lists and more. The scenario for using such a tool is if a server system lacks the capability of generating a CSR keypair on its own. Another Senario would be if large networks […]
Category: 8. SSL Library
Windows Server IIS/Exchange – Intermediate Installation
Add to Favorites You have successfully installed your SSL Certificate on a windows server system although you might be having some trust issues on certain browsers or applications are not fully trusting your SSL Certificate. This may be due to a lack of an intermediate CA certificate file that helps Chain the Trust to your clients […]
What is the CA/Browser Forum?
Add to Favorites The Certification Authority Browser Forum, also known as CA/Browser Forum, is a voluntary consortium of certification authorities, vendors of Internet browser software, operating systems, and other PKI (Encrypted) applications that make the industry guidelines. It governs the issuance and management of SSL and Code Signing digital certificates that chain to a trust anchor root that is […]
Microsoft Lync 2013 – SSL Installation
Add to Favorites Like the majority of server systems, you will install your SSL certificate on the same server where your Certificate Signing Request (CSR) was created. This is because your private key will always be left on the server system where the CSR was originally created. With Microsoft systems, the private key is hidden […]
Microsoft Lync 2013 – CSR Instructions
Add to Favorites To generate a Certificate Signing Request (CSR) for Windows Lync 2013 you will need to create a key pair for your server the public key and private key. These two items are a digital certificate key pair and cannot be separated. On Windows type systems PFX/PKCS12 requests are made, and are stored […]
Total Website Security for Total Confidence
Add to Favorites Symantec™ Extended Validation (EV) SSL Certificates can be a key factor in helping increase customer confidence during online business transactions. More confidence can mean more conversions for customers with EV SSL certificates. Extended validation (EV) SSL assures users that your site is secure and your identity has been authenticated to the […]
Setting up Exchange configuration in Exchange 2010 & 2013
Add to Favorites Setting up the configuration in Exchange 2010 and 2013 configuration will vary depending on your environment. You will need to know and select the Exchange configuration that best works for you and your organization. If you need more support on how the Exchange configuration services best fits you and your environment you will need to […]
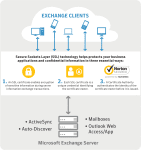
SSL Solutions for Microsoft Exchange
Add to Favorites Microsoft Exchange: How it fits into business Microsoft Exchange: How SSL fits into business applications are essential tools for any business. With the introduction of Microsoft Exchange 2007, 2010 and 2013, businesses are able to leverage constant communication to drive productivity and stay competitive. Along with the new capabilities comes a greater […]
Why every Domain and Sub Domain needs to be validated each time.
Add to Favorites Security practices in issuing a certificate and why every Domain Sub Domain needs to be validated each time: The urgent need for all commercial CAs to implement better security standards, starting with the CA/Browser Baseline Requirements, and the steps that Web browser developers, SSL certificate subscribers, and relying parties can to do […]
Transition from the VeriSign Seal to the Norton Secured Seal
Add to Favorites Same Check. New Name. More Benefits Transition from the VeriSign® Seal to the Norton Secured Seal: In April 2012, the VeriSign Trust Seal will change to the Norton Secured Seal, and will now fall under the newly created group, Symantec Website Security Solutions. Although things may appear different, the high standard of […]