Windows servers use .pfx/.p12 (pkcs#12) files to contain the public key file (SSL Certificate) and its unique private key file.
The Certificate Authority (CA) provides you with your SSL Certificate (public key file). You use your server to generate the associated private key file where the CSR was created.
You need both the public key and private keys for an SSL certificate to work properly on any system. Windows uses the pfx/p12 file to contain these two keys; therefore, if you need to transfer your SSL certificate from one server to another or store it someplace for safe keeping you need to create a .pfx backup.
Depending on the type of Tomcat system you have you may have to perform a conversion of your .pfx keystore into a .jks keystore type to be recognized by Tomcat. Instructions on that conversion are in Step 3 – A.
To backup, export, and move a SSL certificate from Windows IIS to Tomcat systems with its private key perform the following steps.
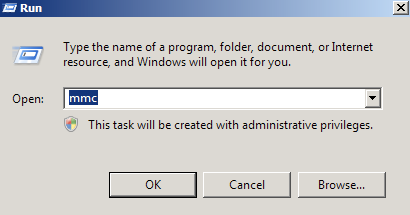
Step 1: Create an MMC Snap-in for Managing Certificates on the IIS 7 system:
- Start > run > MMC.
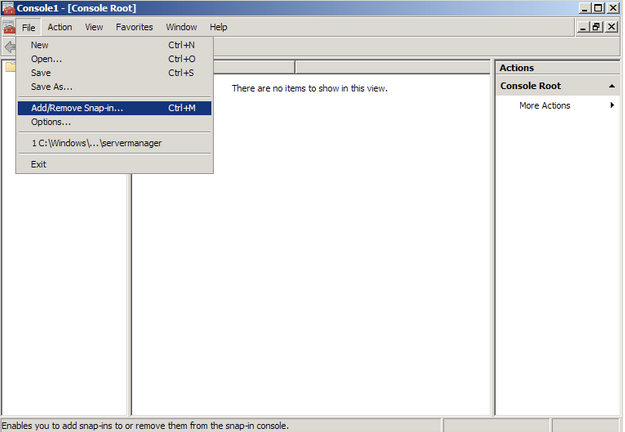
- Go into the Console Tab > File > Add/Remove Snap-in.
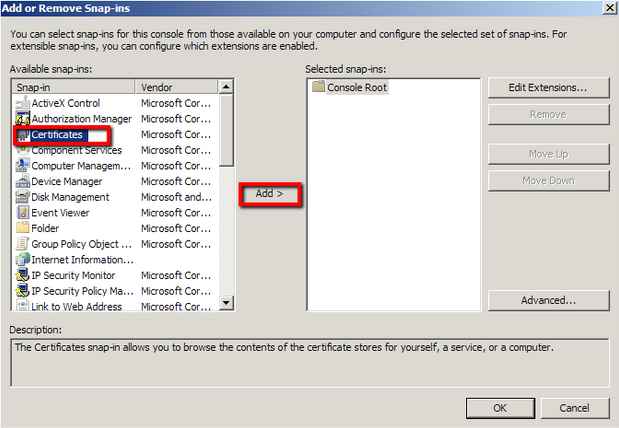
- Click on Add > Click on Certificates and click on Add.
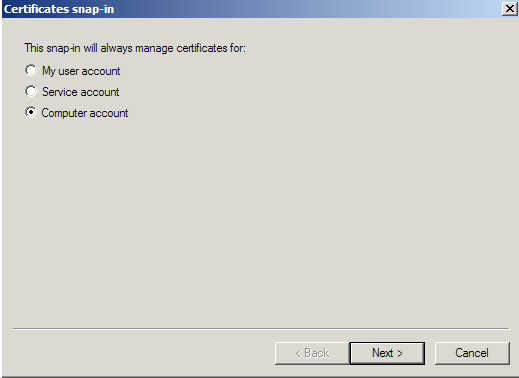
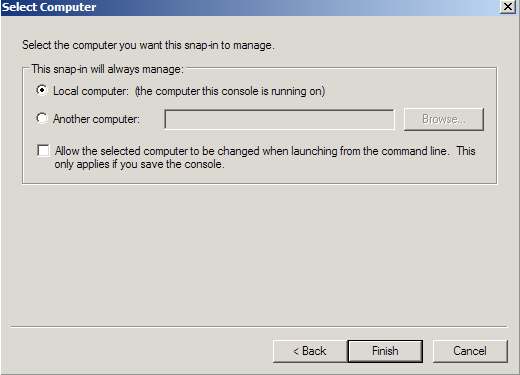
- Choose Computer Account > Next.
- Choose Local Computer > Finish.
- Close the Add Standalone Snap-in window.
- Click on OK at the Add/Remove Snap-in window.
Step 2: Export/Backup certificate to .pfx file:
- In MMC Double click on Certificates (Local Computer) in the center window.
- Double click on the Personal folder, and then on Certificates.
- Right Click on the Certificate you would like to backup and choose > ALL TASKS > Export
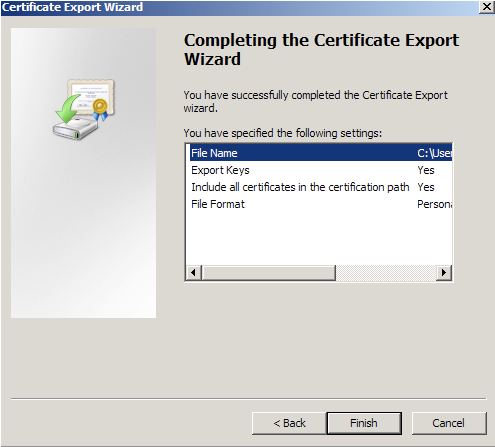
- Follow the Certificate Export Wizard to backup your certificate to a .pfx file.
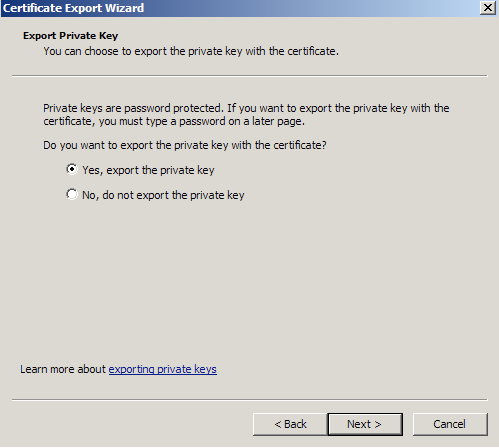
- Choose to ‘Yes, export the private key‘
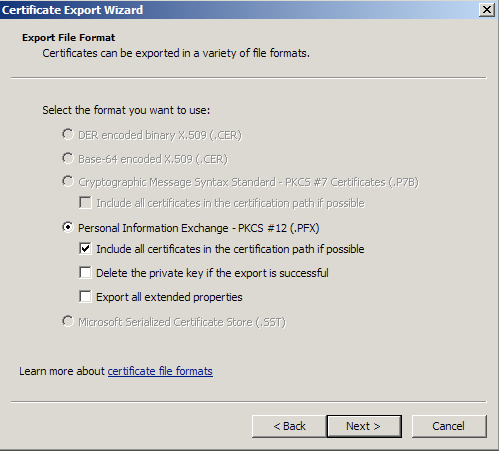
- Choose to “Include all certificates in certificate path if possible.” (do NOT select the delete Private Key option)
- Enter a password you will remember.
- Choose to save file on a set location.
- Click Finish.
- You will receive a message “The export was successful.” > Click OK.
- The .pfx file backup is now saved in the location you selected and is ready to be moved or stored for your safe keeping.
Step 3: Preparing the Tomcat system:
Tomcat systems are very customizable. The directory location and naming of the individual files needed vary depending on your personalized system. Below are generalized instructions. After moving you .pfx file to the tomcat server perform the following.
- On the Tomcat server search and open the Tomcat server.xml file.
- Open the server.xml config file using a text editor (ie. JAKARTA_HOME/conf/server.xml)
Search for the secure element in your config file (try searching for SSL Connector). - Your keystore file name and path is listed under KeystoreFile, and its Password is under keystorePass.
- By default it should look either one of the following A or B:
-
A: Standard Tomcat Systems server.xml using .jks keystores..
- If your Server.xml file looks like the above then perform the following conversion using Keytool on the Tomcat system.
Note: below the naming conversions are generalized. your names will differ. - keytool -importkeystore -srckeystore mypfxfile.pfx -srcstoretype pkcs12 -destkeystore newjkskeystore.jks -deststoretype JK
- After this conversion you will have a new .jks keystore that can be used to specify to the keystore file path and directory.
- Make sure to specify the correct “keystoreFile” directive to the new keystore and the “keystorePass” directive is referencing the correct keystore password.
Note: These directives are case-sensitive! Make sure the letters “F” and “P” in “keystoreFile” and “keystorePass” are in uppercase.
Note: If your keystore contains more than one private key alias, please add the “keyAlias” directive to reference the correct private key alias name. Usually only seen in some standard Tomcat systems that use .jks keystores.
For Example:
keystoreFile=”insert path to the keystore here”
keystorePass=”insert keystore password here”
keyAlias=”insert private key alias here”/>
- If your Server.xml file looks like the above then perform the following conversion using Keytool on the Tomcat system.
-
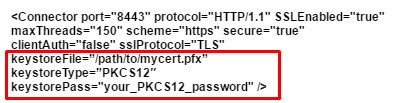
B: Tomcat Systems server.xml able to use .pfx keystores..
- If your Server.xml file looks like the blow example then no need for a conversion your version of tomcat has the capability of using .pfx files.
- After you have figured out what type of keystore your server.xml file requires you are then ready to make the server.xml file point to your .pfx keystore.
- Make sure to specify the correct “keystoreFile” directive to the new keystore and the “keystorePass” directive is referencing the correct keystore password.
Note: These directives are case-sensitive! Make sure the letters “F” and “P” in “keystoreFile” and “keystorePass” are in uppercase.
For Example:
keystoreFile=”insert path to the keystore here”
keystorePass=”insert keystore password here”
- If your Server.xml file looks like the blow example then no need for a conversion your version of tomcat has the capability of using .pfx files.
-
- After you have updated your server.xml file…
- Save the changes.
- Stop and start Tomcat.
Your SSL/TLS certificate is now installed and configured for its website.
If you are unable to use these instructions for your server, Acmetek recommends that you contact either the vendor of your software or the organization that supports it.
Tomcat Support:
For more information, please refer to Tomcat Support