Troubleshooting SSL Certificate Web Browser Errors can vary depending on its cause. The following warnings are presented by web browsers when you access a site that has a security certificate installed (for SSL/TLS data encryption) that cannot be verified by the browser. Typically this is from a self signed certificate created by a server system for default encryption.
Examples
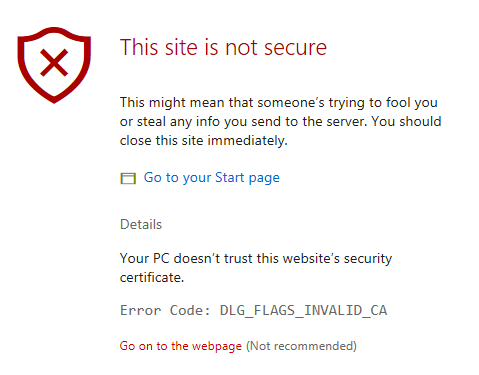
Microsoft Edge: “This site is not secure. This might mean that someone’s trying to fool you or steal any info you send to the server. You should close this site immediately.”
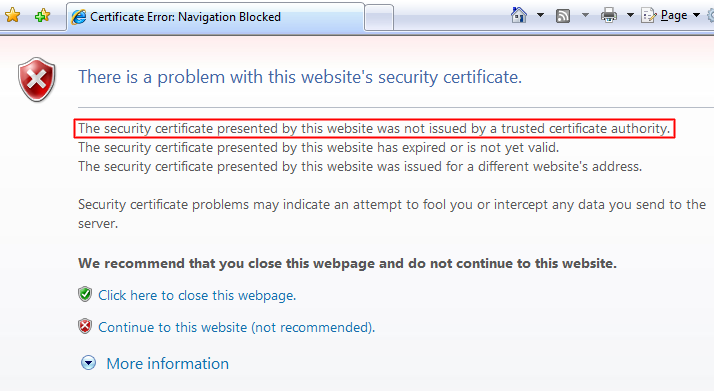
Internet Explorer: “The security certificate presented by this website was not issued by a trusted certificate authority.”
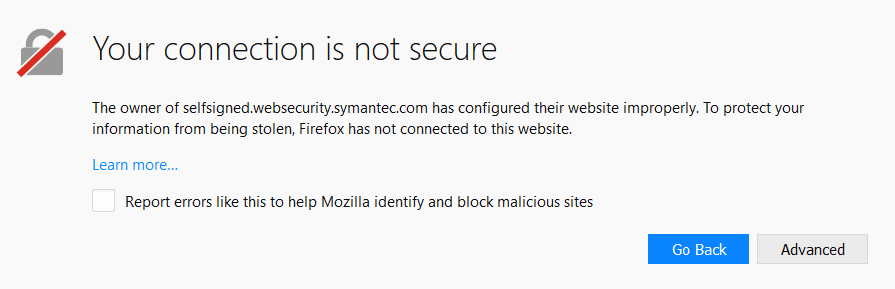
Firefox: “The owner of selfsigned.websecurity.symantec.com has configured their website improperly. To protect your information from being stolen, Firefox has not connected to this website.
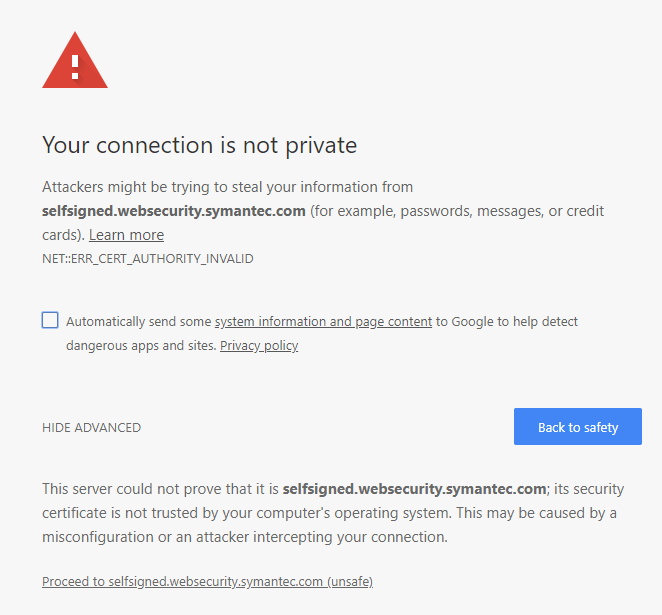
Chrome: “Your connection is not private. Attackers might be trying to steal your information from selfsigned.websecurity.symantec.com (for example, passwords, messages, or credit cards)”
Browsers are made with a built-in list of trusted certificate providers (like DigiCert, Symantec, Entrust, etc.). For some sites, the certificate provider is not on that list. If this is the case, the browser will warn you that the Certificate Authority (CA) who issued the certificate is not trusted. This issue can also occur if the site has a self-signed certificate. While this warning is fairly generic for Internet Explorer, Firefox will distinguish between a certificate issued by the server itself (a self-signed certificate) and another type of untrusted certificate.
If you are the network have an SSL certificate and you receive this error, troubleshoot the problem using the sections below. You do not need to install anything on client devices/applications for an SSL Certificate to work properly. The first step is to use an SSL Certificate tester to find the cause of error.
Self-Signed Certificates
One possible cause of this error is that a self-signed certificate is installed on the server, or Firewall. Self-signed certificates aren’t trusted by browsers because they are generated by your server, not by a CA. You can tell if a certificate is self-signed if a CA is not listed in the issuer field in our SSL Certificate tester.
If you find a self-signed certificate on your server after installing an SSL certificate, we recommend that you check the installation instructions and make sure that you have completed all of the steps. Also, Check any firewall that’s may be interfering. If internally you have installed the certificate on its server system, but with an external certificate checkers are seeing a self signed certificate, you will need to apply the certificate to it.
If you completed all of the installation steps but are still having an issue, you should generate a new CSR from your server (see the CSR creation instructions) and then reissue the certificate in your from your CA. Sometimes the best way to resolve an issue s to start from scratch.
Intermediate Certificate Issues
The most common cause of a “certificate not trusted” error is that the certificate installation was not properly completed on the server (or servers) hosting the site. Use our SSL Certificate tester to check for this issue. In the tester, an incomplete installation shows one certificate file and a broken red chain.
To resolve this problem, install the intermediate certificates (or chain certificate) file to the server that hosts your website. To do that, you may have to contact your SSL Certificate CA. Many CA’s have a Console where you can manage your certificate or will send you an email that should consist of the necessary intermediates. Defending on the server system installation of this intermediate certificate will vary. Follow your server-specific installation instructions to install the intermediate certificate file.
Once you import the intermediate certificate, check the installation again using the SSL Certificate tester. In the tester, an incomplete installation shows multiple certificate files connected by an unbroken blue chain.